How to Remove Galimatimod/Taurus_1.exe [Trojan:Win32/Predator!ml] Spyware + Windows Malware Analysis
Has your computer been infected with the Galimatimod spyware virus? This new malware has some dangerous capabilities, including microphone access and password stealing. Read our analysis below to learn more about how Galimatimod infects Windows computer systems or skip directly to our removal guide.
Galimatimod was first discovered in April, and it’s behavior shares a few striking similarities with calimalimodunator.exe, another spyware virus we covered earlier this year. However, Galimatimod’s more unnoticeable features makes it even more threatening on an unprotected PC. Our malware analysis will reveal how Galimatimod runs its spyware operations on victim computers, how it sends data back to threat actors, and how it can evade antivirus as well as investigation.
General Info:
Filenames - SecuriteInfo.com.W32.AIDetect.malware1.18890.7779, SecuriteInfo.com.W32.AIDetect.malware1.18890.exe, galimatimod, galimatimod.exe, Taurus_1.exe, Taurus_2.exe
File Size - 407,040 Bytes
Compiler/Icon Language - Spanish
File Hash:
SHA-256 - a423314d33b74a166ce89ccef59bd5da0b25a6cfdc4ab59ac0fe157dad3082cd
SHA-1 - f92013c1762eafbbb430892e8cb32356d07e29e6
MD5 - 6d248c611de8a4ab22d9a4cf7e7b1fb3
Librarie(s) Accessed (Windows) - kernel32.dll
Test Sample Used - Malware Bazaar
Possible Malware Family - Taurus Stealer
Disclaimer:
Our extensive malware testing analysis is based on the investigation of the test sample listed above. Since our research involves analyzing file properties and data profiles associated with the Galimatimod malware, our antivirus tool is highly likely to flag new variants and remove file systems changes made by those variants as well as the original sample. That being said, malicious variants may vary and exhibit unique behaviors as well as differing structures not listed in this report. New information about the software behind the sample file may also be made publicly available after this post. Subscribe to the Riserbo Blog to be notified of any updates made on this page.Distribution:
Spyware viruses are designed to target highly-selective information on infected computers. Distribution methods for this type of malware often differ from those used by ransomware or other types. The Galimatimod/Taurus Stealer variant we tested accesses keyboard, microphone, and browser data. This means that the malware’s distribution methods may capitalize on computers with microphones or the Chrome browser installed.
Direct Download - During our virtual machine testing phase of the Galimatimod malware, very little visible activity was seen upon execution of an infected file. Despite this, Galimatimod runs dozens of operations in the background, even after it has “finished” executing. To evade antivirus detection, the virus employs a technique known as software packing which effectively hides its file signature behind encrypted or unreadable data. This technique allows Galimatimod to be distributed online via direct download links, since most antivirus engines will not detect newly packed versions.
Malicious Websites - Buying websites to spread malware is a common distribution tactic for threat actors. Some sites can be bought with cryptocurrency, providing malware developers with relative anonymity when making their purchase. Some sites are also stolen for distribution purposes, especially those with serious vulnerabilities. It’s possible that Galimatimod itself is spread via malicious websites due to the fact that it makes requests to at least one recently domain website during its infection.
Emails - Sending emails with attached malware is another preferred method of distribution among today’s threat actors. Spam emails are known to carry malicious software hidden underneath links or attachments. According to Dataprot, almost 85% of all emails are spam and a lot of this spam contains malware. Galimatimod itself can be smuggled through compressed ZIP files or document macros. Avoid downloading files or navigating links sent by suspicious emails.
Behavior:
Upon running Galimatimod or Taurus_1.exe, no visible processes or windows will appear. Instead, the virus works in the background, silently stealing information behind the scenes. The file may also use Microsoft’s KMS Connection Broker to identify and connect to available desktops. Galimatimod then extracts browser data by searching through the following directories:
- C:\Users\victim\AppData\Local\Google\Chrome\User Data\Default\Web Data
- C:\Users\victim\AppData\Local\Application Data\Application Data\Application Data\Application Data\Google\Chrome\User Data\Default\Login Data
- C:\Users\victim\AppData\Local\Application Data\Google\Chrome\User Data\Default\Cookies
- C:\Users\victim\Local Settings\Application Data\Application Data\Application Data\Google\Chrome\User Data\Default\History
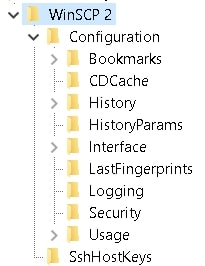
Along with stealing browser data, Galimatimod has the ability to swipe FTP/SSH file transfer login data, a common feature of the Taurus Stealer malware family. It can do this by accessing and reading the Windows registry key for WinSCP:
HKEY_CURRENT_USER\Software\Martin Prikryl\WinSCP 2\Sessions
Note: This key is only present for WinSCP users. With FTP or SSH login data, threat actors can access file servers and spread their malware further.
In order to send stolen data back to Galimatimod’s controllers, this malware uses a very stealthy approach to obfuscate/secure information. Instead of simply sending raw passwords, login data, or etc. to a C&C (Control and Command) server, Galimatimod establishes an encrypted channel first by using Microsoft’s Enhanced Cryptographic Provider. This effectively hides C&C traffic to prevent malicious servers from being taken down or attacked and stops malware analyzers from identifying exactly what kind of data is being sent.
More of Taurus_1.exe or Galimatimod’s capabilities include acquiring the victim’s timezone (possibly used for tracking infections and victim location), screen capturing, keyboard input capturing, microphone monitoring, and antivirus/virtual machine detection. This last feature may indicate that galimatimod.exe behaves differently when executed on a virtual machine (as done in our analysis) to distract analysts from logging real behavior on a physical machine. It should be mentioned that the victim’s timezone is critical data for a virus like Galimatimod or Taurus Stealer which can potentially swipe credit card information. Threat actors will need to use a VPS, or a virtual private server, to use stolen credit cards online and make it appear as though they are making purchases close to the victim’s real location so they can bypass automatic fraud detection software.
Removal:
Removing the Galimatimod virus, Taurus_1.exe, or its other files and variants is very easy to do with the malware removal tool built into our antivirus app, Malscope. Differing removal methods may exist but the following steps are our tested instructions for Galimatimod malware removal:
1. Purchase or download the Malscope Antivirus from our webpage and unzip the installer. If you purchase a yearly plan, you can use the code “taurus1” to get 30% off Malscope, an app that is equipped to detect Galimatimod along with its possible variants and highlight any malicious files it discovers. The discount code will expire in 30 days, so be sure to use it as soon as possible!
2. Run the “Malscope” app and enter the product key you received after your purchase (check your email). If you already have a product key, you may skip the purchasing steps and enter it now.
3. Wait for Malscope to set up its environment. Once controls for the app are loaded, you can begin removing the Galimatimod infection.
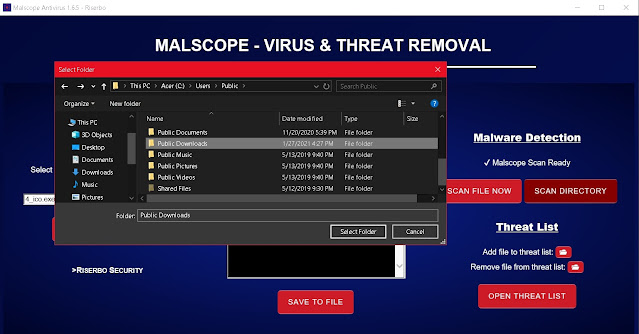
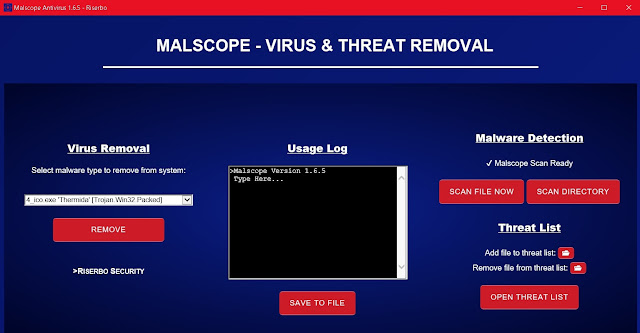
4. Click the drop-down box under “Virus Removal” on Malscope to select a malware type to remove. Click “Galimatimod/Taurus_1 [Trojan:Win32/Predator!ml]” and then press remove. If the Galimatimod virus is or was active on your computer, Malscope will automatically remove all associated files and reverse damages to your system’s settings and execution policies.
5. If you downloaded Galimatimod or Taurus_1.exe by mistake, be sure to scan the directory you saved it to with the “Scan Directory” button. This will prompt you to select a folder which you can scan with a single click. Malscope will automatically mark suspicious files and print them onto the usage log for you to read. You may then choose to delete the files either manually or through Malscope’s “Scan File Now” data removal option.
Prevention:
Since Malscope Antivirus is equipped with the ability to detect Galimatimod, Taurus_1.exe and its variants, we recommend using this tool to prevent an infection as well as removing it. Downloaded executable files should be regularly scanned with Malscope to ensure their safety.Additional Notes:
-Galimatimod may also harvest data from the Windows Mail app by accessing the following registry key:
HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles
-The malware makes requests to three URLs during its attack:
hxxp://legend0.ru/cfg/ and hxxp://legend0.ru/log/
Note: These requests may be domains associated with a Taurus C&C server or they may simply be more obfuscation attempts.
-The image below is the icon present on Galimatimod executables.



![Select the dropdown menu on Malscope and click Galimatimod/Taurus_1 [Trojan:Win32/Predator!ml] to remove the virus](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiKfs_b8eY1s90-2LV1fjHebTyHhPB_uitW5cEjEhSFaEFEXu-SZMnucCwH0qHv5XZi9XGAoJeJTo44LjPxVWNkjBLPFykGQHOEkaTxmb_T2ck07H-NsGu9NnCU2MicnB9fVFv654cZ-6qg/w640-h336/malscope-v-step4.jpg)