Welcome to a complete removal guide for the calimalimodunator.exe virus (otherwise known as A954E0~1.EXE). This new spyware is specifically designed to steal user credentials and harvest sensitive browser data. An infection should be removed as soon as possible. Click here to skip directly to our removal guide.
By making use of a dangerous arsenal of dropped dynamic link library files (DLLs), Calimalimodunator can change your system policies to compromise your environment and swipe data. Our malware analysis will reveal how Calimalimodunator runs its data-stealing operations on victim computers, how it executes dropped files, and how it can evade antivirus and investigation.
General Info:
Filenames - Calimalimodunator.exe, SecuriteInfo.com.W32.AIDetect.malware1.4821.3208, SECURI~1.exe, A954E0~1.exe
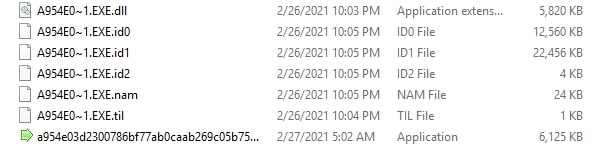
Dropped Filenames - SECURI~1.EXE.dll, A954E0~1.EXE.dll, A954E0~1.EXE.id0, A954E0~1.EXE.id1, A954E0~1.EXE.id2, A954E0~1.EXE.nam, A954E0~1.EXE.til
Total File Size - 6,272,000 Bytes
Possible Malware Origin - Slovakia, Iran
File Hash:
SHA256 - a954e03d2300786bf77ab0caab269c05b75c34d62e0497979bfbb6919befcff5
SHA1 - dfccc553dd00dee74dc212373a82cae24e2648b5
MD5 - 03b1daa2ee50da70c70c779b7471f492
Librarie(s) Accessed (Windows) - kernel32.dll
Test Sample Used - Malware Bazaar
Variants (Disclaimer):
As is common with most malware targeting Windows machines in today’s world, the original Calimalimodunator file will likely join a large list of software variants designed by threat actors to make improvements to the existing source code. Our extensive malware testing analysis is based on the investigation of the test sample listed above. Since our research involves analyzing file properties and data profiles associated with the Calimalimodunator or A954E0~1.exe malware, our antivirus tool is highly likely to flag new variants and remove file systems changes made by those variants as well as the original sample. That being said, malicious variants may vary and exhibit unique behaviors as well as differing structures not listed in this report. Subscribe to this blog to be notified of any updates made on this page.
Distribution:
Spyware viruses are usually designed to target highly-selective information on infected computers. Distribution methods for this type of malware often differ from those used by ransomware or other types. The Calimalimodunator variant we tested accesses browser data from Chrome. This means that Chrome users are an ideal target for the threat actors behind Calimalimodunator and that their distribution methods may capitalize on this fact.
Direct Download - During our virtual machine testing phase of the Calimalimodunator malware, no fake windows or popups were found, indicating that the virus was attempting to disguise itself as legitimate software. For this reason, it’s possible that Calimalimodunator was developed for a specific target or a group of targets that can be physically accessed. After execution, the software immediately drops its malicious files right into the application’s parent directory. From a victim’s perspective, these files would seem highly suspicious, and the malware would be more effective if it were to modify its environment in a carefully selected, hidden directory. If Calimalimodunator or A954E0~1.exe was transported
via flash drive and executed directly on a target computer behind a wall of folders, it could operate largely undetected by the victim.
Malicious Websites - Buying websites to spread malware is a common distribution tactic for threat actors. Some sites can be bought with cryptocurrency, providing malware developers with relative anonymity when making their purchase. Some sites are also stolen for distribution purposes, especially those with serious vulnerabilities. It’s possible that Calimalimodunator itself is spread via malicious websites due to the fact that it makes requests to at least one recently registered website during its infection.
Behavior:
Upon execution, the Calimalimodunator virus immediately drops the following files into its parent directory: A954E0~1.EXE.dll, A954E0~1.EXE.id0, A954E0~1.EXE.id1, A954E0~1.EXE.id2, A954E0~1.EXE.nam, A954E0~1.EXE.til (filenames may vary). Most of these files are not immediately written to and their function is likely to store stolen data harvested from the host computer.
Calimalimodunator then uses PowerShell to write a bypass to the execution policy for a hidden, temporary dropped file. This allows the malware to run its own PowerShell scripts on the targeted system. Windows execution policy normally
restricts these scripts from being executed, however, Calimalimodunator finds a way around this to continue its spyware operations. In addition to bypassing PowerShell execution policy, this malware also scans infected computers to identify antivirus engines, a function which allows Calimalimodunator to behave differently depending on its environment and avoid being studied by an antivirus program or the security analysts behind it.
When it comes to its data-stealing capabilities, Calimalimodunator selects a very particular browser to swipe information from: Chrome. The malware will scan through an infected computer’s Chrome log files to look for browser settings, internet history, cookies, and login data. If this information is sent back to threat actors, it could potentially place all of the victim's online accounts at risk of being hacked.
Cookie stealing (or session hijacking), which involves swiping cookie data and injecting it on another computer to login using saved sessions, is a common tactic hackers use to break into emails. From a compromised email, hackers may then find sensitive banking information or reset some online passwords. For this reason, spyware is extremely damaging to victims and profitable for cyber-criminals. Calimalimodunator is also known to schedule tasks, meaning it can execute its own files or more malicious activities at preset times.
Finally, Calimalimodunator or A954E0~1.exe also accesses the Windows registry during its infection and makes a connection request to the following address: hxxp://pesterbdd.com/images/Pester.png
This domain was registered this January in Hong Kong, and may be linked to Calimalimodunator’s operation, particularly the data transfer stage of its information-stealing endeavors. However, our testing did not confirm this and it is possible that the connection was formed to obfuscate other attempts at transferring data to the threat actor.
Removal:
Removing the Calimalimodunator virus, A954E0~1.exe, or its other files and variants is very easy to do with the malware removal tool built into our antivirus app,
Malscope. Differing removal methods may exist but the following steps are our tested instructions for Calimalimodunator malware removal:
1. Purchase or download the Malscope Antivirus from
our webpage and unzip the installer. If you purchase a yearly plan, you can use the code “calimali” to get 30% off Malscope, an app that is equipped to detect Calimalimodunator along with its possible variants and highlight any malicious files it discovers. The discount code will expire in 30 days, so be sure to use it as soon as possible!
2. Run the “Malscope” app and enter the product key you received after your purchase (check your email). If you already have a product key, you may skip the purchasing steps and enter it now.
3. Wait for Malscope to set up its environment. Once controls for the app are loaded, you can begin removing the Calimalimodunator infection.
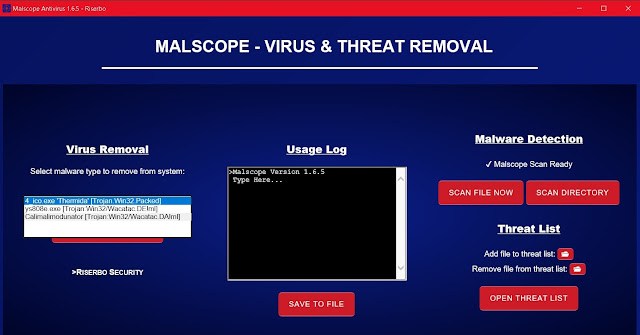
4. Click the drop-down box under “Virus Removal” on Malscope to select a malware type to remove. Click “Calimalimodunator [Trojan:Win32/Wacatac.DA!ml]” and then press remove. If the Calimalimodunator virus is or was active on your computer, Malscope will automatically remove all dropped files and reverse damages to your system’s settings and execution policies.
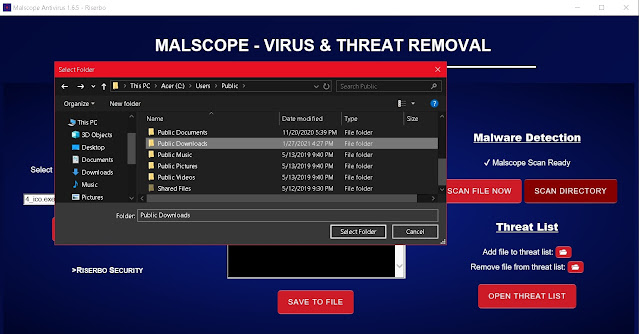
5. If you downloaded Calimalimodunator.exe by mistake, be sure to scan the directory you saved it to with the “Scan Directory” button. This will prompt you to select a folder which you can click and wait for Malscope to scan. Malscope will automatically mark suspicious files and print them onto the usage log for you to read. You may then choose to delete the files either manually or through Malscope’s “Scan File Now” data removal option.
Prevention:
Since Malscope Antivirus is equipped with the ability to detect Calimalimodunator and its variants, we recommend using this tool to prevent an infection as well as removing it. Downloaded executable files should be regularly scanned with Malscope to ensure their safety.
Additional Notes:
-The Calimalimodunator malware was written in Delphi, a dialect of Object Pascal programming languages.
-The compilation system language of Calimalimodunator and A954E0~1 is Slovak, indicating that this virus likely originated from Slovakia.
-”Vsekdag” is the internal legal copyright name of the software used to run Calimalimodunator. This name may refer to a threat actor or malware author, as it has also been used in association with a more infectious spyware known as Calanilimodumator or m8kdtboA0T.exe.
-The image below is the app icon attached to the Calimalimodunator virus.