How to Remove ys808e.exe Virus [Trojan:Win32/Wacatac.DE!ml] + Windows Malware Analysis
Welcome to a complete removal guide and malware analysis for the ys808e.exe virus (Trojan:Win32/Wacatac.DE!ml), also known as Random.exe and “SecuriteInfo.com.BehavesLike.Win32.Trojan.jc.13968”. This Windows Trojan threat was reported on 1/9/2021.
Thanks to an array of analysis/antivirus-evasion tools built into the virus, ys808e malware can not be detected by McAfee, BitDefender, Comodo, or TrendMicro antivirus apps at the time of writing this. Once ys808e.exe is executed on a target PC, it will pursue your private information and make edits to critical Windows system files. Read this article to understand how ys808e works and how to defend yourself against an infection. Click here to skip to our removal guide and security recommendations.
General Info:
Filenames - ys808e.exe, ys808e (1).exe, Random.exe, file.exe, SecuriteInfo.com.BehavesLike.Win32.Trojan.jc.13968, ebe410ca4e64d62e4366e9e1fcf10ad1bf7a99958a847af3d0e9d3850eb003a7.exe (sample name)
File Size - 625,152 Bytes
File Overlay - N/A (Overlay not present)
Possible Malware Family: RedLine Payload
File Hash:
SHA256 - ebe410ca4e64d62e4366e9e1fcf10ad1bf7a99958a847af3d0e9d3850eb003a7
SHA1 - c460f158701e0a5ef5d4eddd9a0257bd1c350c25
MD5 - 9da896f4111c89fee054c1ed44565ecb
Libraries Accessed (Windows) - winhttp.dll, kernel32.dll
Test Sample Used - Malware Bazaar
Variants:
The information written in this article will correspond with the sample testing and static analysis done for the file listed above. Throughout January, variants of the ys808e virus with similar behavioral traits have also been released and sampled. Below are the file hashes (SHA256) that match with these older variants:
Reported on Jan 5 - ecebc42356531d726c29149265632f77431e6d597e88372326d19d821952f565
Reported on Jan 6 - e774c62260c1a3095072af8779ce8d1f7382b41857d93ac3bfc8db6b053ff455
Reported on Jan 8 - 0a5faef2bdcce3d5b58e9062bf8f936596a96eaf0b270ed86cac3033cd922537
Distribution:
Ys808e malware is packed with UPX, a tool used to pack raw executables for supported operating systems in several different formats. UPX works by auto-decompressing executed files and creating a temporary, virtual environment where the original file can run. This tool may have been abused by ys808e.exe malware authors to obfuscate malicious payloads or it may have been used to package code in a way that makes ys808e executable on Windows machines. You might receive ys808e.exe, Random.exe, or a similar file through any of the following mediums:
Emails - Sending emails with attached malware is a preferred method of distribution among today’s threat actors. Spam emails are known to carry malicious software hidden underneath links or attachments. According to Fortinet, up to 1 in 3,000 spam messages can contain some form of malware. ys808e.exe itself can be smuggled through compressed ZIP files or document macros. Please do not attempt to download files or navigate links sent by suspicious emails.
Web Downloads - The distribution method ys808e is most associated with is web downloads. You might find variants of this malware on server addresses or software distributor websites. Since ys808e.exe is not currently detected as malware on most antivirus engines, there’s a good chance threat actors will still be able to spread ys808e across the internet to unsuspecting users.
Behavior:
After opening an app infected with ys808e, the virus will obtain your computer system manufacturer data to test the environment for virtualized software. This behavior indicates an intent to evade analysis since most live malware samples (including ours) are tested on virtual machines. Because of this, it is unclear whether or not ys808e.exe will behave differently on a real, physical Windows computer. If you have experience with this file that differs from our virtually-tested behavioral analysis, please contact us by email. This section of the article will be updated if new data is discovered.
Once ys808e has found your system manufacturer, it will begin calling the Windows API command “GetSystemTimeAsFileTime” in a repetitive loop to likely delay further analysis or detection. In the background, ys808e.exe will also access the registry and harvest all mail client-related data under the following Microsoft Outlook keys:
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\Mail\Microsoft Outlook\Capabilities\Hidden
HKEY_LOCAL_MACHINE\Software\Clients\Mail\Microsoft Outlook\Capabilities
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\Mail\Microsoft Outlook\Capabilities\FileAssociations
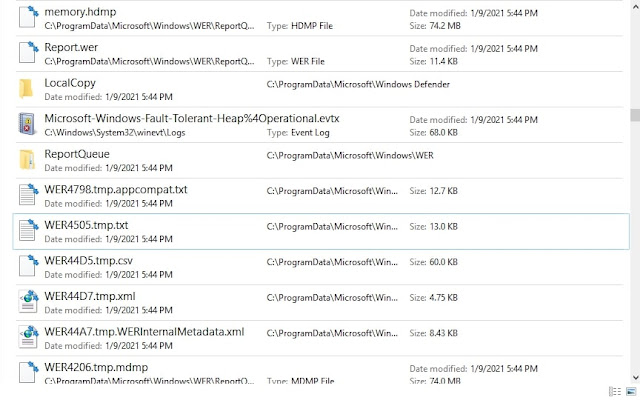
Interestingly, ys808e.exe or Random.exe also activates WerFault.exe, a tool designed by Microsoft for Windows error reporting. Several edits were also made to system Font files during our sample tests of the file. It is currently unclear why this tool was used or why these edits were made.
Some variants of ys808e.exe are also known to spawn network activity by repeatedly testing local connections to 192.168.1.7 through up to 37 various ports. In one instance, the file made a DNS request to oribba.xyz, a domain created very recently and not currently activated in the DNS.
Regardless of some of the seemingly harmless activity ys808e.exe generates, this file and its variants should be taken seriously. The analysis-evading processes behind them suggest a more sinister objective behind this malware operation and ys808e’s behavior on physical computers is yet to be revealed. If you have opened this file by mistake or believe you are dealing with a ys808e infection, read our removal guide below.Removal:
Removing the ys808e.exe virus entirely from a computer system might be difficult, but not impossible. Differing removal methods may exist but the following steps are our tested instructions for ys808e.exe removal:
1. Purchase or download the Malscope Antivirus from our webpage and unzip the installer. If you purchase a yearly plan, you can use the code “ys808e” to get 30% off Malscope (discount will expire on February 11). This app is equipped to detect ys808e.exe along with its older variants and will highlight any malicious files it discovers.
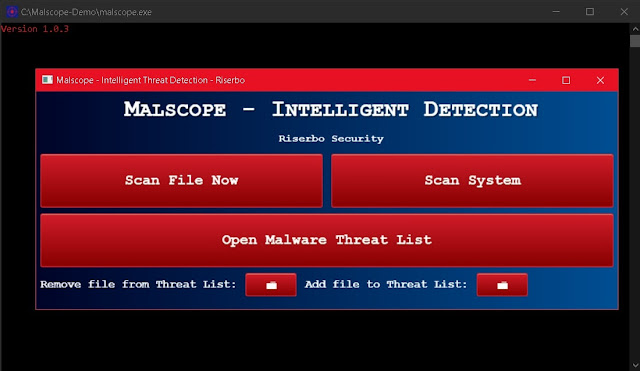
2. Run the “Malscope” app and enter the product key you received after your purchase (check your email). If you already have a product key, you may skip the purchasing steps and enter it now.
3. Wait for Malscope to set up its environment. Once controls for the app are loaded, you can begin removing a ys808e.exe infection.
Prevention:
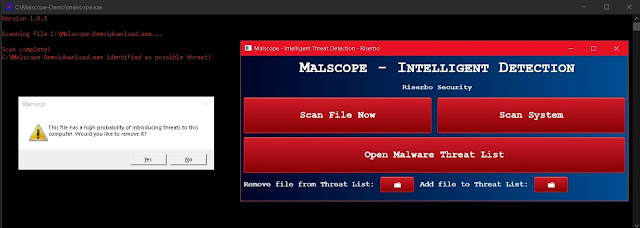
Since Malscope Antivirus is equipped with the ability to detect ys808e and its variants, we recommend using this tool to prevent an infection as well as removing it. Downloaded executable files should be regularly scanned with Malscope to ensure their safety.
Additional Notes:
VirusTotal
-During our static analysis of this virus, we discovered the internal name of the file listed as “vebug.ekze” and the legal copyright of ys808e.exe to be marked as “Copyri (C) 2019, permudationzy”. Similar names have been found within various RedLine password-stealer malware versions. For this reason, we believe it’s possible ys808.exe might be related to this particular malware family.
-Most ys808e variants start or modify a total of 19 Windows processes
-The following file icon is associated with ys808e.exe, Random.exe, and other related files:
-The Porteguese language was found within several ys808e.exe binary/debugging resources
-Update: The domain kypersan16.top has been identified as a live source of the ys808e virus