How to Remove/Prevent 4_ico.exe (Trojan.Win32.Packed) "Thermida" Virus on Windows - Complete Malware Analysis Guide
This is a complete guide for the removal/protection from 4_ico.exe (Trojan.Win32.Packed) virus, a general Windows trojan threat reported on 12/25/2020.
Also known as Thermida, this older malware can still cause serious issues on new Windows computers and an infection should be removed as fast as possible. In this article, we will discuss our analysis of the file as well as the malware’s behavior and you will learn how to prevent and remove this virus. Please click here or scroll down below to find our recommendation and removal tips.
General Info:
File Size - 51,200 Bytes (without overlay), 5,560,102 Bytes (with overlay)
Target Machines - Intel 386 / Compatible / Later
File Hash:
SHA256 - 23b038034753de2b160a1039ad4f724f0cb75d57d0f73af56d592850c82a20cb
SHA1 - ebe90b7d6f1758ec5ba37ac4790ea218b40acda6
MD5 - 55eef1be7b19e0f52556a646368aefc2
Libraries accessed (Windows) - user32.dll, version.dll, kernel32.dll, advapi32.dll, shell32.dll
Test Sample - Malware Bazaar
Distribution:
4_ico.exe is commonly run as a package along with vpn_ico.exe and 6_ico.exe, two separate portable executable files which perform different tasks to help this malware extract data from a compromised system. You might receive a 4_ico package through any of the following mediums:
Emails - A preferred method of distribution among malware developers - spam emails are known to carry malicious software hidden underneath links or attachments. 4_ico.exe itself can be smuggled through compressed files or document macros. Do not attempt to download files or navigate links sent by suspicious emails.
Fake Software - 4_ico’s start behavior suggests an intent to deceive its victims by imitating a legitimate app. The error message (shown above) which appears upon execution is fake, meaning 4_ico.exe is likely duplicating real error messages from similarly named software, such as the Oreans Thermida Protection app. Online downloads can contain the 4_ico.exe payload while pretending to run entirely separate programs.
Distribution Websites - Upon investigation, we discovered an array of online sites 4_ico.exe sends HTTP(S) requests to during its cycle of infection. This article will discuss these websites in more detail below, however it is likely that 4_ico.exe samples themselves also spread across sites built and designed solely for malware distribution.
Behavior:
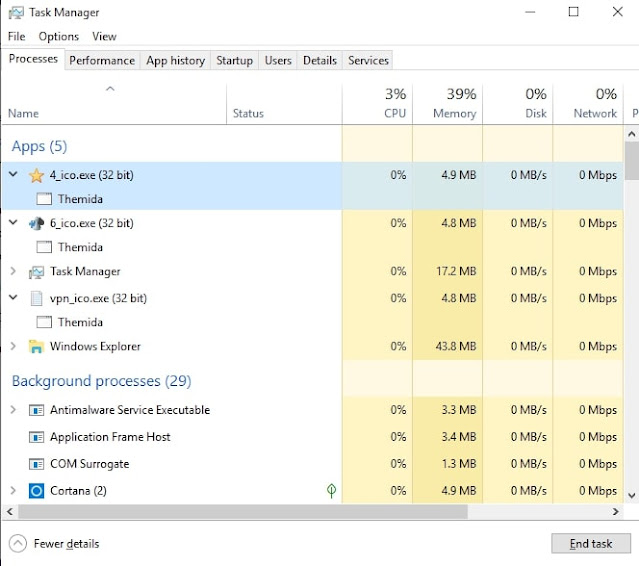
Upon opening the malicious app, 4_ico.exe will immediately run a UAC prompt asking the user for admin privileges. If this request is accepted, 4_ico.exe displays a “Thermida” error message which reads: “A monitor program has been found running in your system. Please unload it from memory and restart your program.” The error message will then duplicate three times, and three separate applications will open and run in the background.
As previously mentioned under “Distribution”, these error messages are likely designed to imitate legitimate software. This is a fairly common tactic, and in this case it even encourages a victim to restart their computer (an action that possibly results in more payload activation). The three programs that run alongside the Thermida windows include “4_ico.exe”, “6_ico.exe”, “vpn_ico.exe”.
Out of these three files, 4_ico.exe results in the most lasting changes on a victim computer. The other two files, 6_ico.exe and vpn_ico.exe, make HTTP(S) requests to the IP-logging websites ip-api.com, 2no.co, and iplogger.org. These websites allow users to capture the IP address of any machine accessing a particular link, which can be dangerous only when used for nefarious purposes. An IP address will reveal information about a network/machine and pinpoint a victim’s general location. The fact that all three of these sites are used in succession suggests that 4_ico.exe is some form of data mining software, although they are also often utilized by threat actor(s) to keep track of infected machines and their locations.
6_ico.exe and vpn_ico.exe also make requests to separate, directly malicious sites in order to download more payloads. While these two scripts run HTTP(S) requests, 4_ico.exe does the heavy lifting for this malware. The sole program can search for, move, and delete files while accessing special folders after receiving administrative privileges on a target Windows computer. Whether or not 4_ico.exe can encrypt files in a ransomware-like fashion is currently unknown. Further tests will be performed, so be sure to subscribe to the blog to be notified of any updates.
System information and clipboard data can also be modified/extracted by 4_ico.exe, making it especially dangerous for individuals storing passwords or sensitive plaintext on their computer.
Finally, 4_ico.exe can make edits under Control Panel settings and escalate privileges for other files. Even after the application it is launched from appears to have ended, malware can still be active as a system process behind the scenes. Windows registry keys will also be affected, so victims of a 4_ico.exe attack will likely face lasting damage to their computers even after initial removal.
Removal:
Removing the 4_ico.exe virus entirely from a computer system might be difficult, but not impossible. Several removal methods may exist but the following steps are our tested instructions for 4_ico.exe removal:
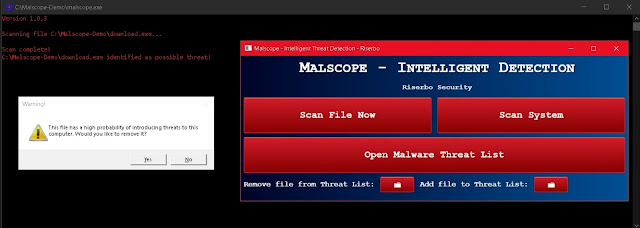
1. Purchase or download the Malscope Antivirus from our webpage and unzip the installer. If you purchase a yearly plan, you can use the code “4ico” to get 50% off Malscope (discount will expire on January 25). This app is equipped to detect 4_ico.exe along with its variants and will highlight any malicious files as viruses.
2. Run the “Malscope” app and enter the product key you received after your purchase (check your email). If you already have a product key, skip the purchasing steps and enter it now.
3. Wait for Malscope to set up its environment. Once the controls for the app are visible, you can begin removing 4_ico.exe
4. Click “Scan File Now” to select any file and scan it for viruses. If a virus is found, Malscope will prompt you to remove it. After clicking yes, “yes” the data for the malicious file will be wiped before it is permanently deleted. Begin doing this for the first file(s) which ran 4_ico.exe - these are most likely in your Downloads folder.
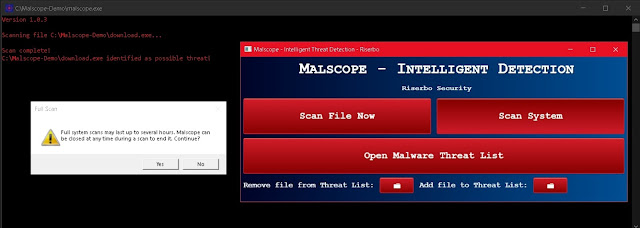
5. Click “Scan System” and wait for Malscope to scan through your entire system. Malscope will automatically filter through files most likely to introduce threats and warn you if they are associated with 4_ico.exe. Remove all files confirmed to be malware.
Prevention:
Preventing a 4_ico.exe infection on your computer is also possible with Malscope. Antivirus may be used to check downloaded files and ensure they are safe to use. As aforementioned, Malscope is equipped with data from our 4_ico.exe analysis, meaning it can detect any files associated with the virus.
VirusTotal
Additional Notes:
-The behavior of this malware indicates that 4_ico.exe was designed for data mining. The files 4_ico.exe creates contain unreadable data which might include system information or specifications that can then be sent to threat actors later with an extraction tool. Access to and modification of the clipboard are also common features of most data mining-related malware today.
-The 4_ico.exe package includes a massive Nullsoft file overlay (over 99% of file ratio). This points to the idea that 4_ico.exe was created with NSIS (Nullsoft Scriptable Install System).
-This virus has reportedly been active since February of 2012, with recent variants hitting target machines around December of 2020.
-All of this malware’s known processes are run from a single thread. A multithreaded performance would indicate a ransomware operation as the culprit behind 4_ico.exe, so it is unlikely that it can encrypt your files on its own. However, 4_ico.exe can still download ransomware payloads via HTTP(S) requests, and this should be taken into account in a prevention plan. Fortunately, you can scan files for ransomware with the Malscope Antivirus, which also happens to be armed with modern ransomware-detection features.